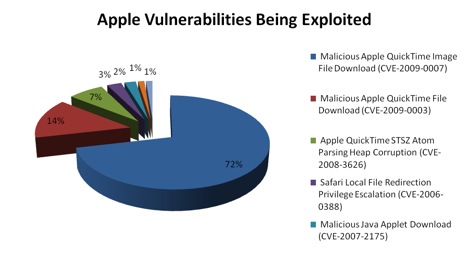
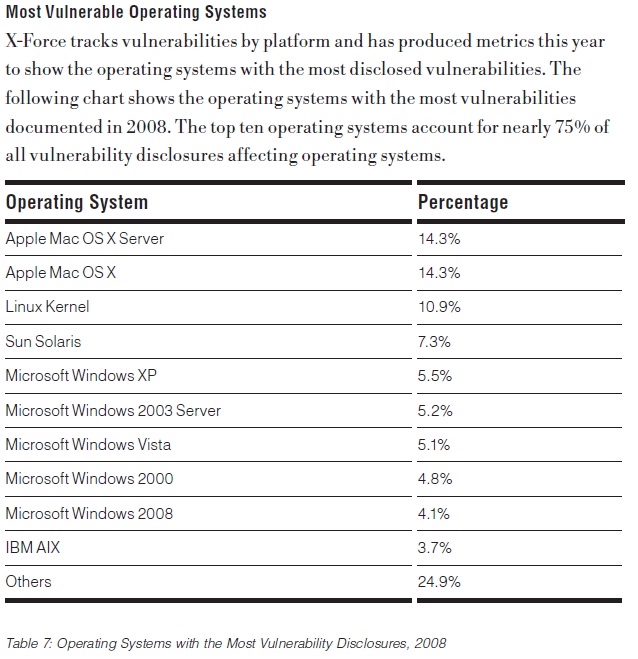
Today President Obama Introduced the Nation's New Cyber Czar, Howard Schmidt. This appointment is in line with President Obama's commitment to protect the Nations Critical Cyber Infrastructure as well as National Security objectives.
Howard Schmidt is a leading authority on Information Security with over 40 years of experience in government, business and law enforcement.


His Qualifications:
Howard will be responsible for coordinating the cyber security initiatives set forth by the White House administration. Additionally, he will have regular access to President Obama and will be a key member of the Presidents National Security Staff.
In His Own Words:
President Obama's 10 Point Cyber Security Plan
For more see: http://www.bankinfosecurity.com/articles.php?art_id=1503
In May of 2009, President Obama laid out the following 10 Point Cyber Security Plan; The appointment of Howard Schmidt allows him to check off another initiative of the plan.
In his White House speech, Obama said he plans to:
"The task I have described will not be easy," Obama said. "Some 1.5 billion people around the world are already online, and more are logging on every day. Groups and governments are sharpening their cyber capabilities. Protecting our prosperity and security in this globalized world is going to be a long, difficult struggle demanding patience and persistence over many years.
"But we need to remember: We're only at the beginning. The epochs of history are long - the Agricultural Revolution; the Industrial Revolution. By comparison, our Information Age is still in its infancy. We're only at Web 2.0. Now our virtual world is going viral. And we've only just begun to explore the next generation of technologies that will transform our lives in ways we can't even begin to imagine."
My Thoughts:
I am glad to see someone with the extensive 40 year background that Howard Schmidt has, just maybe more people will start to take IT security issues a bit more seriously. I wish him the best luck.
Julius
Reference:


Howard Schmidt is a leading authority on Information Security with over 40 years of experience in government, business and law enforcement.


His Qualifications:
- Chief Security Officer for eBay
- Chief Security Officer for Microsoft
- Chief Security Strategist for CERT.org
- U.S. Military
- Police Officer
- FBI
- Appointed by President Bush in 2001 as Vice Chair of the Critical Infrastructure Board and as special advisor for Cyberspace Security for the White House.
- Howard Schmidt is also a CISSP and CISM.
- Professor at Georgia Tech
- Adjunct Distinguished Fellow at Carnegie Mellon
- Distinguished Fellow at Ponemon Institute
- Professor of Research Idaho State
- President of the Information Security Forum.
Howard will be responsible for coordinating the cyber security initiatives set forth by the White House administration. Additionally, he will have regular access to President Obama and will be a key member of the Presidents National Security Staff.
In His Own Words:
President Obama's 10 Point Cyber Security Plan
For more see: http://www.bankinfosecurity.com/articles.php?art_id=1503
In May of 2009, President Obama laid out the following 10 Point Cyber Security Plan; The appointment of Howard Schmidt allows him to check off another initiative of the plan.
In his White House speech, Obama said he plans to:
- Appoint a cybersecurity policy official responsible for coordinating the nation's cybersecurity policies and activities; establish a strong National Security Council directorate, under the direction of the cybersecurity policy official dual-hatted to the NSC and the National Economic Council, to coordinate interagency development of cybersecurity-related strategy and policy.
- Sign off on an updated national strategy to secure the information and communications infrastructure. This strategy should include continued evaluation of Comprehensive National Cybersecurity Initiative activities and, where appropriate, build on its successes.
- Designate cybersecurity as one of his key management priorities and establish performance metrics.
- Designate a privacy and civil liberties official to the NSC cybersecurity directorate.
- Convene appropriate interagency mechanisms to conduct interagency-cleared legal analyses of priority cybersecurity-related issues identified during the policy-development process and formulate coherent unified policy guidance that clarifies roles, responsibilities, and the application of agency authorities for cybersecurity-related activities across the federal government.
- Initiate a national public awareness and education campaign to promote cybersecurity.
- Develop U.S. Government positions for an international cybersecurity policy framework and strengthen our international partnerships to create initiatives that address the full range of activities, policies, and opportunities associated with cybersecurity.
- Prepare a cybersecurity incident response plan; initiate a dialog to enhance public-private partnerships with an eye toward streamlining, aligning, and providing resources to optimize their contribution and engagement.
- In collaboration with other Executive Office of the President entities, develop a framework for research and development strategies that focus on game-changing technologies that have the potential to enhance the security, reliability, resilience, and trustworthiness of digital infrastructure; provide the research community access to event data to facilitate developing tools, testing theories, and identifying workable solutions.
- Build a cybersecurity-based identity management vision and strategy that addresses privacy and civil liberties interests, leveraging privacy-enhancing technologies for the nation.
"The task I have described will not be easy," Obama said. "Some 1.5 billion people around the world are already online, and more are logging on every day. Groups and governments are sharpening their cyber capabilities. Protecting our prosperity and security in this globalized world is going to be a long, difficult struggle demanding patience and persistence over many years.
"But we need to remember: We're only at the beginning. The epochs of history are long - the Agricultural Revolution; the Industrial Revolution. By comparison, our Information Age is still in its infancy. We're only at Web 2.0. Now our virtual world is going viral. And we've only just begun to explore the next generation of technologies that will transform our lives in ways we can't even begin to imagine."
My Thoughts:
I am glad to see someone with the extensive 40 year background that Howard Schmidt has, just maybe more people will start to take IT security issues a bit more seriously. I wish him the best luck.
Julius
Reference:
- http://www.whitehouse.gov/blog/2009/12/22/introducing-new-cybersecurity-coordinator
- http://www.scmagazineus.com/howard-schmidt-appointed-white-house-cybersecurity-coordinator/article/160110/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+SCMagazineHome+%28SC+Magazine%29&utm_content=Google+Reader